Understanding JSON Web Token (JWT)
Understand how JSON Web Tokens (JWT) work for secure API authentication by breaking down their structure, lifecycle, and use cases in modern web apps
Introduction
Imagine you’re going to an event, and instead of showing your ID every time you want to enter,
you get a special badge. That badge is your ticket to move around freely no need to keep proving who you are.
JWT (JSON Web Token) works the same way in the digital world! It’s like a secure badge that proves you’re authorized to
access certain parts of a website, without needing to constantly log in or check in.
What I Will Cover in This Article
I) What is JWT
Jwt is a secure string defined by an open standard ( RFC 7519 ) , It help us transmitting information as a claims (json object) between two parties (client and server) in a secure way , it’s a small sized token that encapsulates all necessary information within itself , unlike traditional sessions-based authentication that store the session data in the server , the jwt store all required authentication details inside the token itself this is what makes it highly recommended for stateless authentication systems where the server don’t store the session data but instead of this , the authentication is managed through the token that are verified with each request
II) Structure of JWT
The jwt includes three parts , header , payload and the Signature and each parte of them is Base64Url encoded and combined using a dot (.)
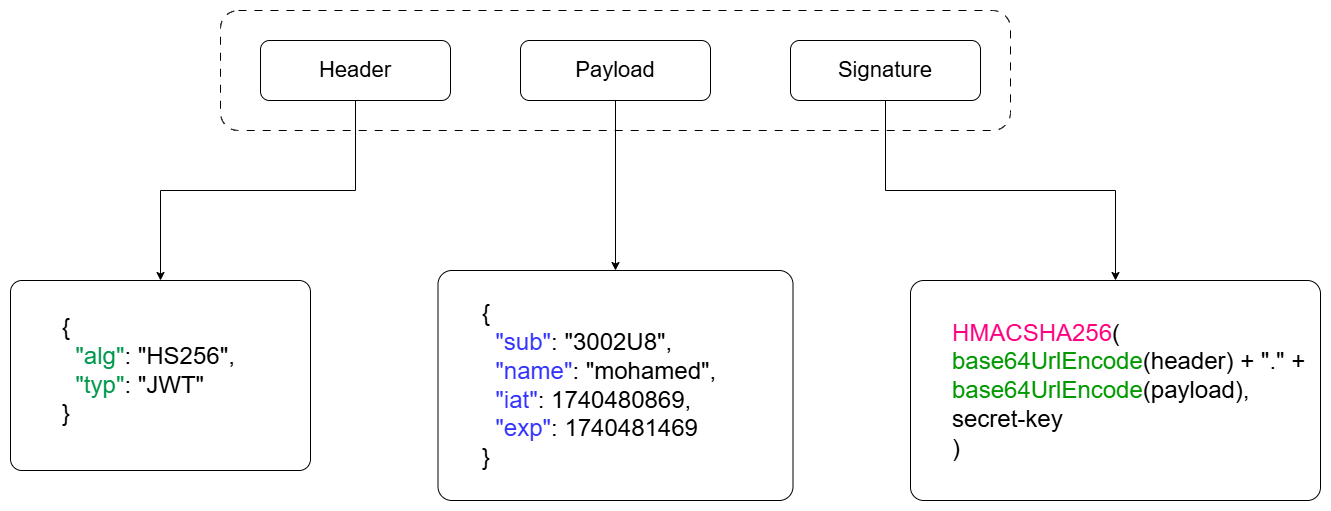
- Header :
The header contains the metadata about the token , which it decide the algorithm used for the token (HS256, RS256) and the type of the token (jwt)
Example :
{
"alg": "HS256",
"typ": "JWT"
}
- Payload :
The payload contains information about the user (claims) and the status of the token itself , these information should be authenticated by the server
It can be predefined and standardized claims recommended by the JWT specification (RFC 7519)
For example :- iss (Issuer): Identifies the entity that issued the JWT.
- sub (Subject): Identifies the subject (usually the user) of JWT.
- exp (Expiration Time): Defines when the token expires.
- nbf (Not Before): The token is valid only after this time.
- iat (Issued At): The time when the token was issued.
And of course it may include custom information about the user for example username , email
But you should be carful about these information by avoid add sensitive data in the payload like a password or bank information of the user because the payload can be readable using some tools by everyone who has the access to the token
Example of the payload :
{
"sub": "mohamedbelalia.dev@gmail.com",
"name": "mohamed",
"iat": 1740480869,
"exp": 1740481469
}
-
Signature :
The signature is the security mechanism that used to verify that the token not changed and comes from trusted source
Its generated by taking the base64Url of the header and the base64Url of the payload concatenating them with a dot and adding a secret key as three element , and then signing the result using a cryptographic algorithm such as HS256 or RS256
So when the server receives the JWT token it recalculate the signature using the same method and compares it with the included signature , if the two signatures are match so the token is valid , otherwise it is rejected
Example :
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret-key
)
III) How JWT Works
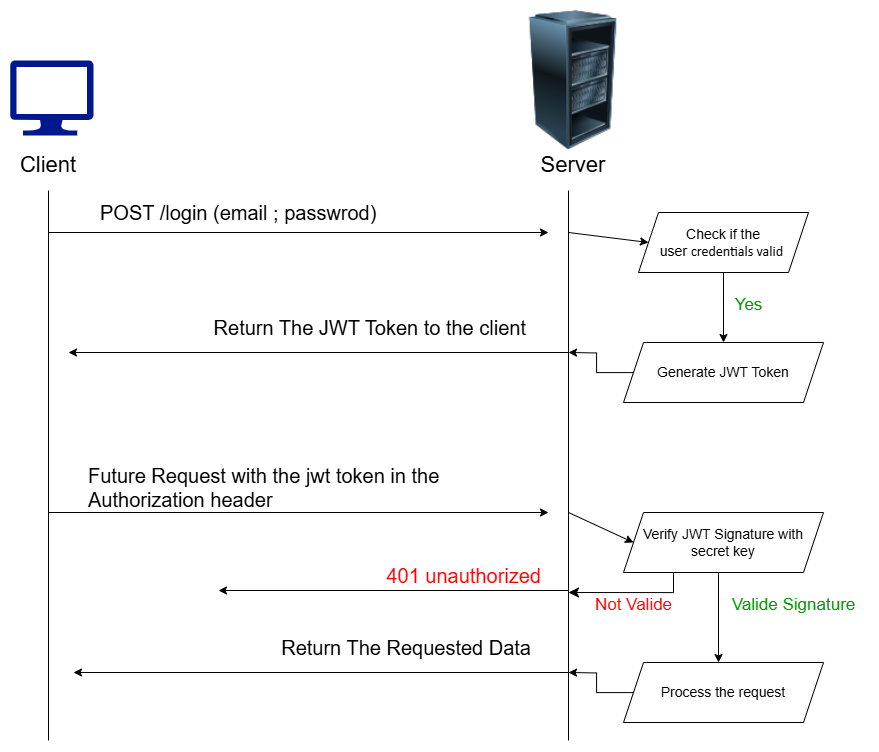
- The first step is when the user logs in with their credentials (email and password)
- Then the server receive that credentials and verify if it stored in the database , if it valid credentials it generate a jwt token
- Then send the jwt token to the client , the client may store it in cookies or local storage
- So when the client store the jwt token it should inject it in each request to the server in the Authorization header
- And the server now will verify the token when it receive any request then decide if the token is validate or not to process the request or not
IV) Why We Should Use JWT
-
Stateless authentication : One the main advantages of jwt is the stateless authentication where the server don’t need to maintain session data for each loged in user and making it scalable
-
Cross-Domain Usage : Jwt is perfect for Single sign on application where the user can login only once and access multiple applications without login again for each one , like when we login in our google account we can access gmail , google drive and youtube and other Google services without needing to re-enter our credentials
-
Compact and Efficient : The jwt can be easily transmitted in the http headers or URLs thanks to the small-size of it
-
High Performance : Reduces database queries compared to session-based authentication.
V) Best Practices for Using JWT
-
Short Expiration Times : Use short expiration times so if the token is stolen it can’t be used for long
-
Store JWTs Securely : Keep tokens in HTTP-only cookies which can’t be accessed by JavaScript instead of local storage to avoid hacking attempts like XSS (Cross-Site Scripting).
-
Always Use HTTPS : This ensures that no one can steal your token by listening to network traffic.
Conclusion
JWT is a great way to handle login and security in web apps it’s fast, easy, and works well across different systems. But, like leaving your house keys in the wrong hands, a poorly managed JWT can be a security risk. If you don’t store it safely or let it last forever, hackers might open your dooe That’s why it’s important to set short expiration times, store tokens securely, and use strong encryption. Think of JWT like a VIP pass—use it wisely, keep it safe, and don’t let the wrong people get their hands on it! Done right, it makes security smooth and reliable.